VPNs were created back in the late 1990s to allow site-to-site connection by virtualizing network access at the TCP/IP level.
The primary use-case at the time was to connect various corporate offices into a unified network.
Since then, VPNs have grown in popularity and have been used for many more use-cases - many of which depart significantly from the original intent and function of the technology.
So much so that the average person likely associates VPNs with anonymous Internet access.About the authorEyal Dotan is the Co-Founder and CTO of Cameyo, the virtual application delivery provider that delivers any Windows apps to any device, from the browser.
Eyal holds 8 U.S.
patents in the field of computer software - security, and prior to Cameyo he was the creator of ViGUARD, one of the first Host Intrusion Prevention (HIPS) software solutions, which was acquired by Ivanti.
Eyal also created and lectured the Logical Attack and Protection program at EPITECH European Institute of Technology, in Paris.Even within the IT circle, VPNs have become the default choice for many use cases, often due to a lack of a better solution.
Remote work is a popular use case, and in light of the Covid-19 outbreak, many companies are rushing to deploy VPNs to enable employees to work remotely.But depending on the scenario for remote work, VPNs are not always the right approach, especially if users are not using IT-managed and hardened devices - which is increasingly common.
In fact, for many companies, VPNs can mean higher risk, degraded user experience, and loss of productivity.
For these scenarios, lets examine a new approach named NoVPN.
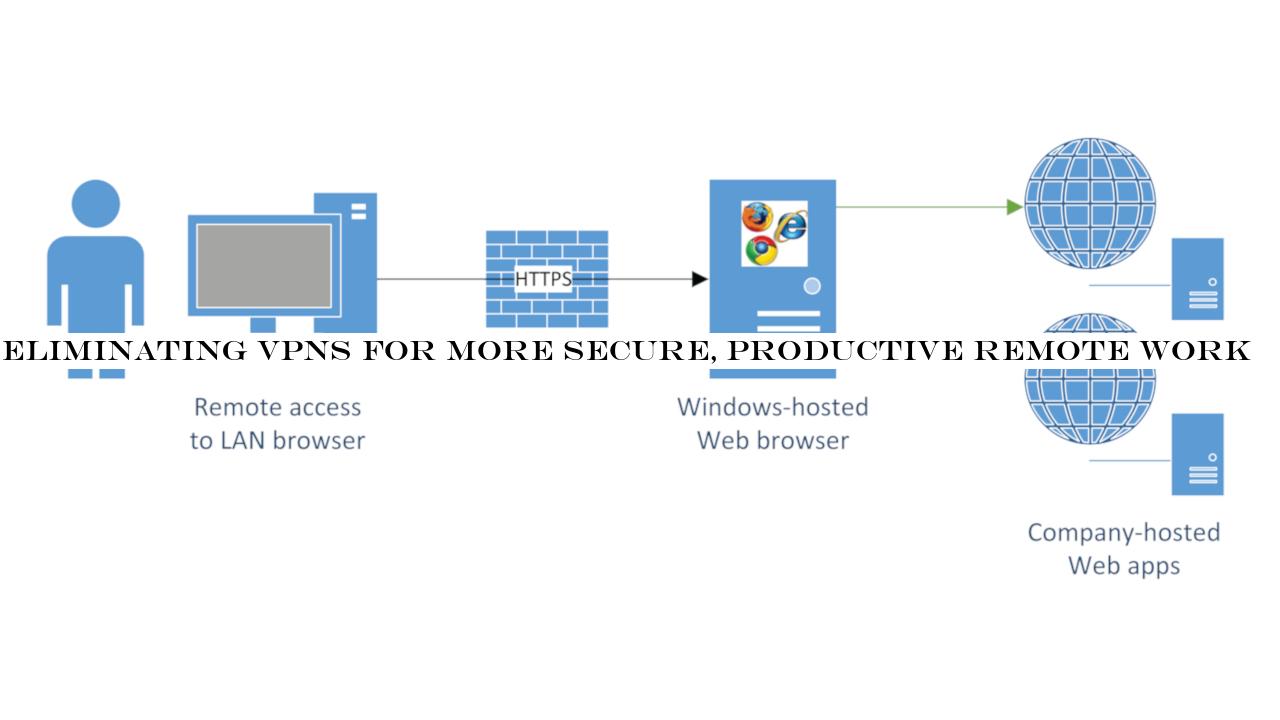
But first, lets take a look at the traditional role of VPNs.VPN: full-stack TCP/IP virtualizationWhen users authenticate into their companys VPN, a virtual network interface is created.
Traffic from the users device is then redirected into - from the companys network.
Any application on the users device can then access the companys network - including printers, files shares, servers - databases, intranet-based web apps, and legacy apps.For companies whose remote workers use personal devices and/or only need to access web - legacy apps to be productive, VPNs are often a mismatch.
They introduce higher costs, more complex infrastructure, and a larger surface of attack.
And when it comes to remote work, people usually dont need access to the other items (beyond web and legacy apps) because:Company printers are usually not needed by remote workersFile shares have other options for remote access, including cloud storage - app-based accessSensitive servers are more vulnerable when the network is accessed by remote employees using personal devicesOne security decision I've seen is allowing the installation of your organizations virtual private network (VPN) software on an employees home computer for remote access.
While some security professionals may think of this as an acceptable practice, this policy is high risk with an undesirable attack vector when permitting access into your environment, said Morey Haber, of the Forbes Technology Council, in an article prior to the Covid-19 outbreak.Hence for many companies, enabling remote work - securely - is about providing access to the business-critical Intranet web apps and/or legacy apps employees need to be productive.
In these organizations, the NoVPN approach may be a better fit.NoVPN: remote app renderingIn 2020 - unlike the late 1990s when VPNs were created - many apps are web-based.
Virtualizing TCP/IP just for redirecting HTTP traffic becomes ineffective and costly.
As for legacy apps that serve TCP/IP clients, their delivery to remote locations can be simplified too, as proven by virtual application delivery platforms that provide access to Windows apps from the browser.NoVPN is a modern approach for securing the delivery of apps by providing remote app rendering in a simple, secure, and user-friendly way.
A server (virtual or physical) is installed within the companys premises, allowing workers to remotely access the required applications, starting with the browser.
The browser is published for remote access.
NoVPN then renders a remote session onto this browser, through HTML5.
In other words, the companys browser is rendered inside the end-users browser, allowing users to browse as if they were inside the companys network.
Sessions are rendered through HTTPS, hence secured with multi-session concurrency support.(Image credit: NoVPN)Non-disruptive workflowWith NoVPN, users simply go to a dedicated URL provided by their IT team.
This begins an HTML5-rendered RDP session of the company-hosted web browser, taking them to the companys web app or portal page.
The user navigates through the remote browser, which looks like a normal browsing session.
The browsers clipboard access is enabled so that users can copy and paste between their computer and the remote session.
Similarly, files can be transferred to and from the users device in a controlled way (based on IT preferences and policies).From a user experience perspective, NoVPN is better than VPN because there is no need to connect / disconnect to a VPN session each time they need to access critical apps.
The rest of the users Internet use goes through their regular browser (not the company-hosted one), meaning faster Internet access for the user and lower network overhead for IT.From a security perspective, NoVPN has significant advantages.
Unlike VPNs, apps on the users device dont have access to the companys network.
This reduces risks related to personal apps, exploits, and malware on the users personal devices, which are not managed by IT.
Browsers are inherently isolated from the users device and file system.
Whether the user has malware, Trojan horses, vulnerable apps or is targeted by hackers, the companys network assets remain safe.Also, deploying a VPN is similar to opening all of the company networks ports to any application on the remote users device.
Hence it requires a full-blown network security audit and hardening.
From dividing the network into subnetworks to reinforcing passwords, closing unnecessary ports and more, the security preparations for deploying VPNs is a considerable project in and of itself.
With NoVPN this isnt required as only the accessible apps - web apps are published, requiring just an HTTPS port forwarding to the internal host.(Image credit: NoVPN)NoVPN for legacy TCP/IP appsDespite web apps, companies may think they need VPNs to enable legacy TCP/IP client-server apps.
Such apps have their own servers which open a TCP/IP port within the companys network, into which dedicated desktop apps connect and work with.
But just like with the web browser, these applications can easily be rendered by the users browser remotely instead with NoVPN.VPNs and remote workingThe COVID-19 outbreak has put pressure on an unprecedented number of companies to establish remote work policies.
Most of them havent had a chance to consider all the issues and security risks involved - like the fact that it is easier for hackers to attack a home user than a corporate network.When those home users are connected through VPNs, the companys data is at risk of theft and more.
If your remote workers use personal devices, operating on an unsecured home network, you should reconsider the approach.
The shift to remote work is here to stay and will outlast the COVID-19 outbreak, so it is critical that you weigh your options and determine if VPNs truly solve the security, user experience, and productivity issues of your new remote workforce.v5afvhApbvGMbaNZRAGbUL.jpg?#

 17
17